| Version 5 (modified by , 4 years ago) ( diff ) |
|---|
Network Device Configuration Management - Oxidized
In this lab you will install Oxidized and integrate it with LibreNMS.
Requirements:
Ubuntu 20.04 Server with LibreNMS installed (Use the provided VM) Gmail account with 2-Step Verification On.
Oxidized Installation
Since most of the tasks in this lab require you to be "root", the first thing you should do is to connect to your server and start a root shell.
sudo su apt update apt-get install ruby ruby-dev libsqlite3-dev libssl-dev pkg-config cmake libssh2-1-dev libicu-dev zlib1g-dev g++ sysctl -w net.ipv6.conf.all.disable_ipv6=1 sysctl -w net.ipv6.conf.default.disable_ipv6=1 sysctl -w net.ipv6.conf.lo.disable_ipv6=1 gem install oxidized gem install oxidized-script oxidized-web
Oxidized Configuration
Create the oxidized user.
useradd -s /bin/bash -m oxidized
Continue with oxidized user.
Setup Oxidized Service
Run the following commands as root user.
cp extra/oxidized.service /etc/systemd/system mkdir /run/oxidized chown oxidized:oxidized /run/oxidized systemctl enable oxidized.service
Start oxidised service
systemctl start oxidized
Restart oxidised service
systemctl restart oxidized
View status of oxidised service
systemctl status oxidized
LibreNMS Integration
Create Token
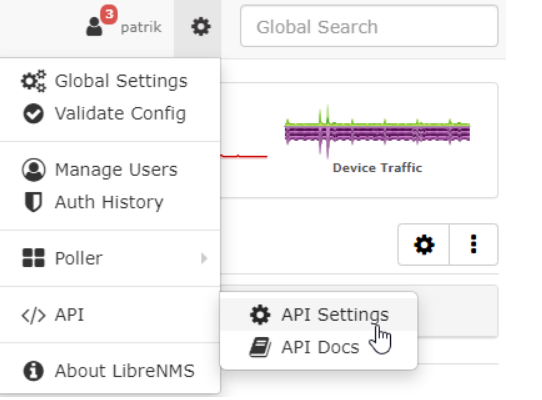
Login to LibreNMS web GUI.
Go to Settings -> API Settings
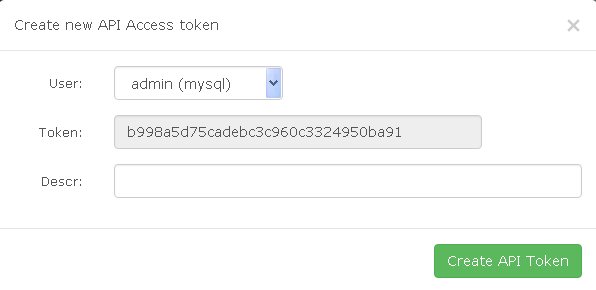
Click on 'Create API access token'.
Click 'Create API Token'.
Postfix Installation
Postfix will be installed to have email notification of configuration changes.
apt install postfix
Select Internet Site to enable Postfix to sent and receive mails and press Enter to proceed.
Put a suitable domain name for System mail name and proceed.
Postfix Configuration
Here Postfix will be configured to send email to your Gmail account.
vim /etc/postfix/main.cf
smtpd_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtpd_tls_security_level=may
smtp_tls_CApath=/etc/ssl/certs
smtp_tls_security_level=may
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
smtp_tls_CAfile = /etc/ssl/certs/ca-certificates.crt
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
myhostname = librenms
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = $myhostname, librenms-demo.com, librenms, localhost.localdomain, localhost
relayhost = [smtp.gmail.com]:587
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
inet_protocols = all
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
smtp_sasl_security_options = noanonymous
Attachments (11)
- librenms api settings.png (53.7 KB ) - added by 4 years ago.
- librenms create token.png (6.0 KB ) - added by 4 years ago.
- select app.png (25.8 KB ) - added by 4 years ago.
- oxidised librenms.png (81.7 KB ) - added by 4 years ago.
- librenms oxidized.png (15.4 KB ) - added by 4 years ago.
- history.png (27.3 KB ) - added by 3 years ago.
- notification.png (34.9 KB ) - added by 3 years ago.
- mail name.png (11.8 KB ) - added by 3 years ago.
- internet site.png (35.0 KB ) - added by 3 years ago.
- device config.png (23.6 KB ) - added by 3 years ago.
- diff.png (20.1 KB ) - added by 3 years ago.
Download all attachments as: .zip