| Version 3 (modified by , 7 years ago) ( diff ) |
|---|
Basic Firewall Setup
In the Lab setup, you have already created a VM for pfSense and has added new network adapters and configured them with UDP tunnels. Here we will install the pfSense in the created VM and do some basic configurations of pfSense.
Pfsense Setup
The pfSense project is a free, open-source tailored version of FreeBSD for use as a firewall and router with an easy-to-use web interface. For the easiness of the lab, we have created a pre-installed virtual machine and the basic vm network setup has been covered during the basic lab setup session.
First Bootup
After booting, you will get a console screen with available options and summaries. pfSense console configuration interface has the basic configuration options in pfSense. You can select these options by typing their index number and pressing enter.
Assign Interfaces
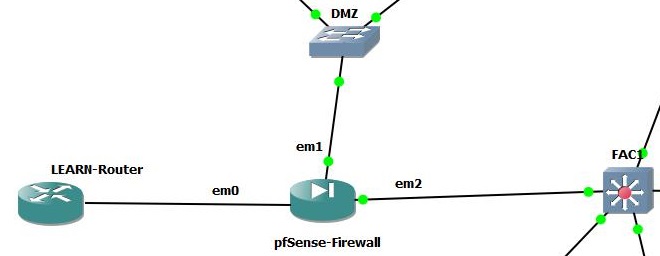
In this pfSense installation, we will have three networks connected to the pfSense firewall as WAN, LAN, and DMZ. Further, at the pfSense console you will see three network interfaces as em0 , em1 and em2 just above the console configuration options. Here em0,em1 and em2 are consecutively the adapter 1, adapter 2 and adapter 3 in pfSense VM. At the Lab setup, we have already connected em1 to DMZ and em2 to LAN (FAC1) through UDP tunnels. Further em0 connected to the WAN side. By now we will have a network setup as follows. ( You may vefiry these by cross checking the mac addresses shown in the console against the addresses assigned in the virtualbox vm settings network tab. )
- Adapter 1 --> em0 --> WAN
- Adapter 2 --> em1 --> DMZ
- Adapter 3 --> em2 --> LAN
But please notice that within pfSense configuration still, we have not assigned any of the above em0,em1,em2 interfaces to any of WAN, LAN or DMZ networks yet.
- To assign interfaces to networks press 1 and enter
- It will ask you to assign VLANs, press N as we don't need it now.
- Then it will ask which interface to use as WAN interface. To select em0 as WAN interface type em0 and press enter
- Next, it will ask which interface to use as LAN interface. In this setup, we are going to assign em1 as DMZ interface. But by default pfSense installation we will not have an interface called DMZ by default. For an example, multi-port pfSense will have interfaces WAN, LAN, OPT1, OPT2 .. etc. Since our pfSense have three interfaces it will have interfaces WAN, LAN, and OPT1. To create a DMZ interface we will have to log in to web configurator of the pfSense. In order to do that we will use a GUI machine which is connected to DMZ. With initial pfSense setup, only LAN connected machines are allowed to access pfSense web configurator. Due to this reason temporarily we will assign em1 as the pfSense LAN interface so that we can log in pfSense web configurator through GUI. To select em1 as LAN interface type em1 and press enter.
- Next we will avoid assigning em2 to any interface. Later from pfsense web configurator, we will assign em1 as DMZ interface and em2 as LAN interface. For now, just enter to skip the step.
- Do you want to proceed? press y to say yes and enter
Assign WAN IP addresses
- To change the interface IP address press 2 and enter
- WAN IP is set by DHCP by default. To change the WAN interface IP Address press 1 and enter.
- We are going to have a static IP for WAN Interface. So press n and enter to avoid pfSense to configure the interface IP by DHCP.
- Enter the WAN IP address assigned to you as 192.248.7.PQ and enter. Give a subnet mask as 24 and gateway in the next steps. You can find your IP allocation from the IP table, WANv4 gateway for the lab is 192.248.7.254
- Do the same for IPv6 address, WANv6 gateway for the lab is 2401:dd00:2000::ffff
- Press n and enter to disable http on WAN interface
- You will be prompted back to main interface after pressing Enter when it prompts.
Assign DMZ IP addresses
- To change the interface IP address press 2 and enter
- To change the LAN interface IP Address press 2 and enter.
- Enter the LAN IP address as 192.168.XY.254. Enter the subnet mask as 24. We are going to have this IP address as our DMZ's gateway IP. Do not give any parameters to the gateway on LAN. Just press enter.
- Enter the LAN IPv6 address as 2401:DD00:20XY:1::FFFF. Enter the subnet mask as 64. We are going to have this IP address as our LAN's gateway IPv6. Do not give any parameters to the gateway on LAN. Just press enter.
- To enable DHCP server on DMZ press y and press enter
- For this workshop, our DMZ DHCP range is 192.168.XY.10 to 192.168.XY.50. Give start and end IP addresses in the next steps.
- When it asks to enable DHCP for IPv6 press n as we are not to enable dhcpv6 at this time
- Press n and enter to disable http on WAN interface
- You will be prompt back to the main interface.
You have now set up both WAN and DMZ IP addresses.
Reset WEB Configurator password
This step is optional as This step will reveal you the default user name and password for the web configurator. Press 3 and enter.
Above the line 'Do you want to proceed' you will see the default username and password on the web access. Note down the default password and Press n
WebUI and Basic Configurations
pfSense by default allows you to do the configuration through its web user interface. Initially, LAN segment hosts are allowed to log in and therefore you need to have a device connected to its LAN. Please double check your VM network connections before powering on the GUI vm. If all settings are satisfying, power on Virtual Machine. Now log in to your GUI vm and from your GUI desktop firefox app, browse to http://<pfSense-DMZ-address>
Default admin / pass are admin / pfsense
The first visit to the WebGUI will be redirected to the setup wizard, which is also accessible at System > Setup Wizard. Proceed through the wizard as follows:
- Step 1: Next
- Step 2:
- Hostname: pfsense
- Domain: instXY.ac.lk
- Primary DNS Server: 192.248.7.254
- unset Overide DNS option
- Step 3:
- Time Server hostname: 192.248.1.161
- Timezone: Asia/Colombo
- Step 4: Next
- Step 5: Next
- Step 6: Change admin password to the class password given for the lab
- Step 7: Reload
- Finish
- Accept
After that, you will be directed to the Dashboard.
Adding Firewall rule to allow connectivity from Lab
By default only hosts from pfSense LAN connected network is allowed to connect pfSense Web configurator. No connections will be allowed from any other interface. To allow connections from our Lab network (WAN side) we will add the below firewall rule.
go to Firewall > Rules > WAN > Add to end
- Action: pass
- Interface: WAN
- Address Family: IPv4
- Protocol: TCP
- Source: Network : 192.248.7.0/24
- Destination: WAN address
- Destination Port: Any, Any
- Log: ticked
- Description: Allow pfSense access from lab
Save and Apply Changes
Now you can use your host machine's web browser to log in to your pfSense web configurator using its WAN address.
Switch the LAN interface to back to DMZ
Now we have assigned the em1 interface to pfSense LAN interface. Since we can now login to pfSense web configurator through host machine we will again switch LAN and DMZ networks. In order to do that we have to Rename LAN interface to DMZ. Now Login to pfSense through host machine using WAN IP address. Go to Interfaces -> LAN Change the description LAN to DMZ. Save and apply changes.
Adding the LAN interface
Now pfSense do not have a LAN interface. The remaining interface em2 is assigned to an interface called OPT1. We will now rename the OPT1 to LAN.
Go to Interfaces -> OPT1
Change the description to LAN. Save and apply changes. Now we have all the em0, em1 and em2 assigned to pfSense's WAN, DMZ and LAN respectively.
Assign IP address to LAN
Now we can assign LAN interface an IP from web interface.
Go to Interfaces -> LAN Ipv4 Configuration Type : Static IPV4 Ipv4 Address : 10.XY.0.2 , Prefix length : 30 Ipv4 Upstream gateway : none
Add internal route
Add a firewall rule to allow from LAN to outside
go to Firewall > Rules > LAN > Add to end
- Action: pass
- Interface: LAN
- Address Family: IPv4
- Protocol: any
- Source: Network : 10.XY.0.0/16
- Destination: any
- Log: ticked
- Description: Allow outside from LAN
Dashboard
The pfSense dashboard is the main page of the firewall, and it makes monitoring various aspects of the system easy. Returning to the dashboard can be accomplished by clicking the logo in the upper left, or by navigating to Status > Dashboard. The Dashboard is composed of Widgets, each of which display information about a different area of the firewall including,
- Firewall Logs
- Gateways
- Interface Statistics
- RSS Feed
- Services Status
- System Information
- Thermal Sensors
- Traffic Graphs
- Wake on LAN
A widget can be added to the dashboard by clicking + at the top of the screen, then choosing the widget from the list. Once the widget appears, its placement may be changed by dragging its title bar to another location on the screen. The widget will snap into place in one of two columns, and can be reordered as desired.
Click Save Settings at the top of the screen after making any widget layout changes.
Some widgets will have their own settings, which may be accessed by pressing the wrench icon in their title bar. To save these settings use the Save button inside the widget, not the button at the top of the page.
General Setup
Some basic/common settings are available under System > General Setup. Some useful settings are,
- Hostname: The name by which this pfSense router is known. Should only include the portion before the first “.”.
- Domain: The domain name in which this pfSense is used. Together with the hostname, this will form the Fully Qualified Domain Name (FQDN) of the firewall.
- DNS Servers: The gateway selection for DNS servers is primarily used for Using Multiple IPv4 WAN Connections.
- Time Zone:
- NTP Time Server:
- Language: The language to use for the GUI. Default is English
- Theme: Changes the look and feel of the pfSense GUI, but not the functionality
Interfaces
In this menu we can re-do assigning interfaces, assigning IP addresses etc. As we have already done that using CLI, we will skip this.
Attachments (1)
- Network1.jpg (23.2 KB ) - added by 7 years ago.
Download all attachments as: .zip